Protection Mechanism in 802.11n
References:
When ever a new wireless standard is introduced, the new devices' transmissions cannot be decoded by the older devices. When 802.11g came into existence, the OFDM transmissions by 802.11g devices cannot be decoded by the older 802.11b /802.11devices. Hence in order to protect the newer 802.11g devices from older 802.11b devices, protection mechanisms were introduced in 802.11g 's standard.
In a ERP BSS where 802.11/802.11b coexist, protection mechanism has to be enabled. This is indicated by setting the bits 'Use Protection' and 'non Erp Present' bits in the ERP information element of the beacon. ERP stations know that they need to use the protection frames prior to sending OFDM frames based on this.
In the case of 802.11n, HT transmissions needs to be protected if there are older stations ( b/a/g) present that cannot interpret HT transmissions. Also, HT Green field stations should use protection mechanism when non-GF stations are present in the BSS. If 20 Mhz HT stations are present in a 20/40 MHz BSS, the 20/40 MHz capable stations should use protection mechanism to prevent the 20 MHz only station transmit at the same time.
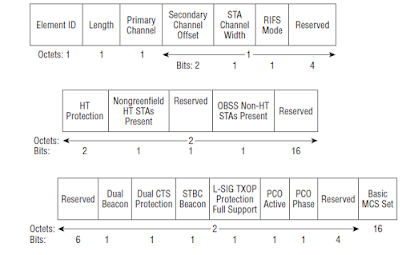
The "HT Protection " and "Non-greenfield STAs Present" fields in the HT Information Element present in the beacon frame are used to indicate the protection requirements for HT transmission.
There are 4 operating Modes (0,1,2,3) . The HT protection field in the HT IE is a 2 bit field that can be set to any of the four values.
Mode 0 : HT No protection Mode : In this mode all the stations in the BSS are either HT 20 MHz or HT 20/40 MHz capable stations. So no protection mechanism is required. However ff there are non GF stations present, the HT-GF station should use a protection mechanism
Mode 1: HT Non Member Protection Mode : In this case all the stations in the HT BSS are HT stations. If there is an overlapping BSS with a 802.11a AP or 802.11g AP , that interferes with HT BSS, then protection has to happen. The case may be:
a) The AP in HT Bss may receive a beacon from a 802.11a AP in 5GHz or a 802.11a client transmission
b) The AP in HT BSS may receive a beacon from 802.11b/g AP or a client transmission in the 2.4GHz
Mode 2: HT 20 MHz protection Mode : In this case, all the station in the BSS are HT stations with Ht 20 or HT 20/40 MHz capability. Protection mechanism has to start when and Ht 20MHz station associates to the HT 20/40 MHz capable AP. In this case, the HT 20/40 MHz capable stations must use protection mechanism before transmitting so that the 20 MHz capable HT stations are aware of the transmission
Mode 3: Non HT Mixed Mode : In this mode, in a single HT BSS, if l non-HT station or legacy stations ( 802.11b/g in 2.4 GHz or 802.11a in 5 GHz) associate , then protection mechanism has to start.
Whenever RTS-CtS ot CTS-self control frames are sent prior to sending HT frames, these frames are sent at a modulation that will be decoded by the stations that need to defer their transmissions . In other words legacy stations from which HT stations have to protected from. For example if both 802.11b and 802.11g stations are present in the BSS, then the control frames will sent at 11b rates, ie the least phy rate.
Types of Protection
1. RTS-CTS using a legacy rate
2. CTS-Self using legacy rate
3. L-SIG TXop protection
This type of protection is called as Phy layer spoofing
The HT Mixed Mode frame format has a HT preamble preceded by a Legacy preamble. The L SIG field of this Legacy preamble has a rate field and a length field. This length sub filed along with the rate sub field is used to control the duration that the non-HT devices need to defer the transmission for.
In this mode of transmission, the rate is always set to 6Mbps.The length field represents a duration corresponding to the length of the rest of the PPDU, ie HT -Preamble, HT-Header and Data.
The idea is that when the legacy station read the preamble, the duration value is calculated from the rate and the length sub-field of the L-SIG field. The transmission is deferred based on calculated duration value from the length and rate sub field.

Comments
Post a Comment